System Group: 7 Powerful Insights You Must Know
Welcome to the ultimate guide on ‘system group’—a concept reshaping how organizations, tech infrastructures, and communities operate. Whether you’re a tech enthusiast, business strategist, or curious learner, this article unpacks everything you need to know in a clear, engaging, and authoritative way.
[ez-toc]
Understanding the Core Concept of System Group

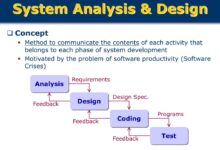
The term system group may sound technical, but its implications stretch far beyond IT departments. At its core, a system group refers to a structured collection of interconnected components—be they people, software, hardware, or processes—that function cohesively to achieve a defined objective. Think of it as a digital or organizational ecosystem where every part plays a role in maintaining balance and efficiency.
Definition and Origin of System Group
The concept of a system group originated from systems theory, a multidisciplinary framework developed in the mid-20th century by thinkers like Ludwig von Bertalanffy. Systems theory posits that entities are best understood not in isolation, but as part of larger, interdependent networks. In computing, the term evolved to describe user access groups within operating systems—such as Unix or Linux—where permissions are assigned collectively. Over time, it expanded into organizational behavior, project management, and enterprise architecture.
Today, a system group can refer to:
- A set of users with shared access rights in an operating system
- An organizational team responsible for maintaining IT infrastructure
- A cluster of integrated software modules working together
- A business unit structured around a specific technological platform
Key Characteristics of a System Group
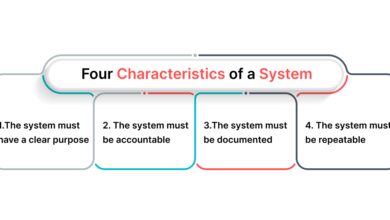
What makes a system group distinct from other organizational or technical constructs? Several defining traits set it apart:
- Interdependence: Each component relies on others to function effectively.
- Defined Boundaries: A system group has clear inputs, outputs, and operational limits.
- Hierarchical Structure: Roles and permissions are often layered, especially in IT contexts.
- Feedback Mechanisms: Performance is monitored and adjusted based on real-time data.
- Scalability: Designed to grow or shrink based on demand.
“A system is never a collection of things but a way of seeing the world.” – Gerald Weinberg, software engineering pioneer.
System Group in Information Technology
In the realm of IT, the term system group takes on a more technical meaning, particularly in operating systems and network administration. It’s a foundational concept for managing access control, security, and resource allocation.
User and Group Management in Operating Systems
Modern operating systems like Linux, Windows, and macOS use system groups to streamline user permissions. For example, in Linux, every user belongs to one or more groups, such as sudo, www-data, or docker. These groups determine what files a user can read, which services they can modify, and whether they can execute administrative commands.
The command groups username reveals which system groups a user belongs to. Similarly, administrators use usermod -aG groupname username to add users to a system group. This granular control enhances security by adhering to the principle of least privilege.
For deeper insights into Linux group management, visit the official Linux Documentation Project.
Role-Based Access Control (RBAC) and System Groups
System groups are central to Role-Based Access Control (RBAC), a security model widely used in enterprise environments. RBAC assigns permissions based on roles rather than individual users. For instance, a ‘Developers’ system group might have access to code repositories, while the ‘Finance’ group can only access accounting software.
Benefits of RBAC include:
- Reduced administrative overhead
- Improved compliance with regulatory standards (e.g., GDPR, HIPAA)
- Fewer permission-related errors
Organizations using Microsoft Azure or AWS IAM (Identity and Access Management) rely heavily on system groups to enforce RBAC policies at scale.
System Group in Organizational Structure
Beyond technology, the idea of a system group applies powerfully to business and organizational design. Companies are increasingly adopting system-based thinking to improve efficiency, innovation, and resilience.
How Companies Use System Groups for Efficiency
Leading organizations structure teams as system groups—cross-functional units with shared goals, tools, and accountability. For example, a DevOps team is a system group combining developers, operations engineers, and QA specialists. They use shared pipelines, monitoring tools, and deployment scripts to deliver software faster and more reliably.
Such groups operate under a unified workflow, often supported by platforms like Jenkins, GitLab CI/CD, or Kubernetes. The system group model reduces silos, accelerates decision-making, and improves service delivery.
Case Study: System Group at Toyota
Toyota’s famed Toyota Production System (TPS) is a prime example of organizational system groups in action. Work cells are designed as self-contained units where teams manage their own quality control, inventory, and problem-solving. Each cell functions as a mini-system group, optimizing flow and minimizing waste.
This approach contributed to Toyota becoming one of the most efficient automakers globally. The key lesson? When people, processes, and tools are aligned as a cohesive system group, performance soars.
System Group in Software Architecture
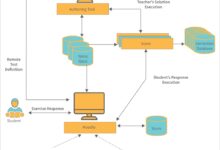
In software development, system groups manifest as modular components or microservices that communicate through APIs. This architectural style enables scalability, fault isolation, and independent deployment.
Microservices and System Group Design
Microservices architecture breaks down large applications into smaller, loosely coupled services—each acting as a system group. For example, an e-commerce platform might have separate system groups for:
- User authentication
- Product catalog
- Order processing
- Payment gateway
- Notification engine
Each system group runs independently, uses its own database, and can be developed and scaled separately. This reduces the risk of system-wide failures and allows teams to innovate faster.
Netflix is a well-known adopter of this model. Their engineering blog details how they manage hundreds of microservices as distributed system groups: Netflix Tech Blog.
API Gateways and System Group Communication
When multiple system groups exist, they need a way to communicate securely and efficiently. API gateways serve as the central hub for routing requests between system groups. Tools like Kong, AWS API Gateway, or Apigee help manage authentication, rate limiting, and monitoring across system group boundaries.
For instance, when a user places an order, the frontend system group sends a request to the API gateway, which then routes it to the order processing and payment system groups. This ensures clean separation of concerns and enhances maintainability.
Security Implications of System Group Management
While system groups enhance efficiency, they also introduce security risks if not managed properly. Misconfigured permissions or overly broad access can lead to data breaches or insider threats.
Common Security Risks in System Groups
Some of the most prevalent security issues include:
- Overprivileged Groups: Users granted more access than needed.
- Orphaned Accounts: Former employees still belonging to active system groups.
- Group Nesting Complexity: Deep hierarchies making permission audits difficult.
- Lack of Monitoring: No logging or alerting on group membership changes.
A 2023 report by CyberArk found that 74% of breaches involved access to privileged accounts—many of which were tied to poorly managed system groups.
Best Practices for Securing System Groups
To mitigate risks, organizations should adopt the following best practices:
- Implement Just-In-Time (JIT) access for sensitive system groups.
- Conduct regular access reviews and audits.
- Use Multi-Factor Authentication (MFA) for group administrators.
- Automate user lifecycle management with Identity Governance tools.
- Enforce the principle of least privilege across all system groups.
The National Institute of Standards and Technology (NIST) provides comprehensive guidelines on securing identity and access management: NIST SP 800-53.
System Group in Cloud Computing
Cloud platforms like AWS, Google Cloud, and Microsoft Azure have redefined how system groups are created, managed, and scaled. In the cloud, system groups are often abstracted as resource groups, projects, or organizational units.
AWS IAM Groups and Policy Management
In Amazon Web Services (AWS), IAM (Identity and Access Management) allows administrators to create system groups with custom policies. For example, a ‘Developers’ group might have read/write access to S3 buckets and EC2 instances, while a ‘Read-Only’ group can only view resources.
IAM groups simplify permission management across thousands of users and services. Policies are written in JSON and can be version-controlled, audited, and shared across accounts.
Google Cloud Projects as System Groups
Google Cloud organizes resources into projects, which function as system groups. Each project has its own set of users, roles, budgets, and monitoring settings. This isolation prevents configuration drift and enhances security.
For example, a company might have separate projects (system groups) for:
- Development
- Staging
- Production
- Data Analytics
This structure ensures that changes in one environment don’t accidentally affect another. Learn more at Google Cloud Projects Overview.
Future Trends in System Group Evolution
As technology advances, the concept of system group is evolving to meet new challenges in automation, AI, and decentralized systems.
AI-Driven System Group Optimization
Artificial Intelligence is beginning to play a role in optimizing system group performance. Machine learning models can analyze access patterns, predict resource needs, and automatically adjust group memberships based on behavior.
For instance, an AI system might detect that a developer frequently accesses database logs and recommend adding them to the ‘DBA’ system group—subject to approval. This proactive approach reduces friction while maintaining security.
Decentralized Identity and Blockchain-Based System Groups
With the rise of Web3 and decentralized identity (DID), future system groups may no longer rely on centralized directories like Active Directory. Instead, blockchain-based systems could allow users to prove membership in a system group via cryptographic credentials.
Projects like Microsoft’s ION and the Decentralized Identity Foundation are pioneering this shift. In such models, a user’s identity and group affiliations are stored on a distributed ledger, giving them control over who can verify their access rights.
The Rise of Autonomous System Groups
Looking further ahead, we may see autonomous system groups—self-managing clusters of AI agents and services that dynamically form, reconfigure, and dissolve based on task requirements. These would operate with minimal human intervention, adapting in real time to changing conditions.
Imagine a disaster response system where drones, sensors, and communication nodes automatically form a temporary system group to coordinate rescue efforts. This vision is already being explored in military and emergency response research.
How to Implement a System Group Strategy
Whether in IT, business, or software development, implementing an effective system group strategy requires careful planning and execution.
Step-by-Step Guide to Creating a System Group
Follow these steps to establish a robust system group framework:
- Define Objectives: What should the system group achieve?
- Identify Components: Who or what will be part of the group?
- Assign Roles and Permissions: Use RBAC principles to define access levels.
- Choose Tools and Platforms: Select appropriate software (e.g., Active Directory, IAM, Kubernetes).
- Document Policies: Create clear guidelines for membership, access, and audits.
- Train Stakeholders: Ensure all members understand their responsibilities.
- Monitor and Iterate: Use logs and feedback to improve the system group over time.
Tools and Platforms for Managing System Groups
Several tools can help manage system groups effectively:
- Microsoft Active Directory: For on-premise user and group management.
- Azure AD / Microsoft Entra ID: Cloud-based identity and access management.
- Okta, Auth0: Identity platforms with strong system group support.
- Puppet, Ansible: Configuration management tools for automating group policies.
- Hashicorp Vault: For managing secrets and dynamic access within system groups.
Explore Ansible’s documentation on managing Linux groups: Ansible Group Module.
Common Misconceptions About System Group
Despite its widespread use, the term ‘system group’ is often misunderstood or oversimplified.
Myth 1: System Group Only Applies to IT
While the term originated in computing, it’s now used across disciplines. In sociology, a system group might describe a community with shared norms and feedback loops. In logistics, it could refer to a supply chain network. The core idea—interconnected elements working toward a goal—applies universally.
Myth 2: Bigger Groups Are More Efficient
Contrary to popular belief, larger system groups often suffer from communication overhead and reduced agility. Research shows that optimal team size for system groups is between 5–9 members, aligning with Dunbar’s number and Amazon’s “two-pizza rule.”
Myth 3: System Groups Are Static
Many assume system groups are fixed entities. In reality, the most effective ones are dynamic—adapting to new members, technologies, and objectives. Agile teams, for example, frequently reconfigure their system group structure based on sprint goals.
What is a system group?
A system group is a structured collection of interconnected components—such as users, software, or processes—that work together to achieve a common goal. It is used in IT for access control, in organizations for team efficiency, and in software architecture for modular design.
How do system groups improve security?
By implementing role-based access control (RBAC), system groups ensure users only have the permissions they need. This reduces the risk of data breaches and insider threats. Regular audits and least-privilege policies further enhance security.
Can system groups be automated?
Yes. Tools like Ansible, Puppet, and cloud IAM services allow organizations to automate the creation, management, and removal of system groups. Automation improves consistency, reduces errors, and scales efficiently.
Are system groups only used in technology?
No. While common in IT, the concept applies to any organized system—such as business teams, supply chains, or social networks—where structure and interdependence enhance performance.
What’s the future of system groups?
The future includes AI-driven optimization, decentralized identity via blockchain, and autonomous system groups that self-organize. These advancements will make system groups smarter, more secure, and more adaptive.
In conclusion, the concept of a system group is far more than a technical detail—it’s a powerful framework for organizing complexity in our digital and organizational worlds. From securing cloud environments to streamlining business operations, system groups enable efficiency, security, and scalability. As technology evolves, so too will the ways we design, manage, and leverage these interconnected systems. By understanding and applying the principles of system groups, individuals and organizations can build more resilient, adaptive, and high-performing structures for the future.
Further Reading: